What to Know About the Tea Hack
Kalamazoo, MI | August 8, 2025
- Tea Dating Advice, a women-only dating safety service, was hacked in late July
- 72,000 images were leaked — including 13,000 verification selfies and driver’s licenses, and 59,000 images from posts and messages
- A second attack occurred July 28–29, exposing 1.1 million private messages from users
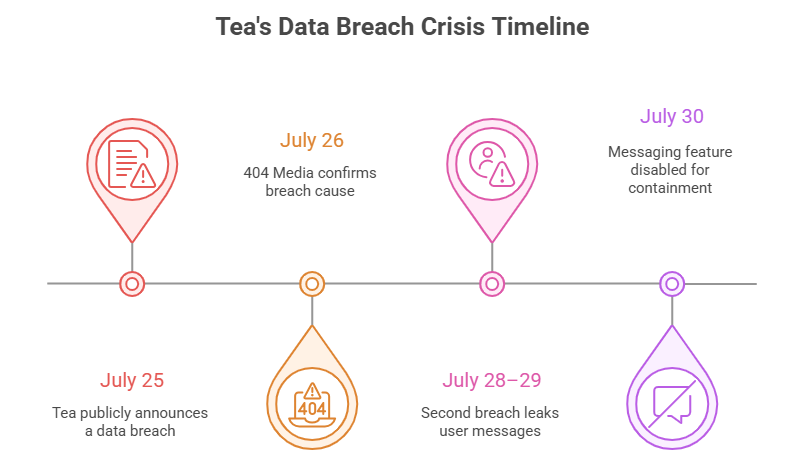
On July 25th, the dating advice app Tea announced that it experienced a major data breach.
At the time, the app ranked at the top of the Apple Store charts, with over 1.6 million users when the breach was announced. But just days after the first attack was discovered, a second breach took place sometime between July 28th and 29th.
Here’s what you need to know about what happened, and what it could mean for you.
How The Tea Hacks Happened (In Plain Language)
Fundamentally, the first Tea hacks were made possible due to mismanaged cloud storage.
When setting up their data “buckets” (essentially, a folder stored in the cloud) in the cloud service Firebase, Tea left one bucket completely unsecured. The storage bucket was neither encrypted nor password protected. Essentially, anyone with a few basic Firebase tools would be able to access sensitive user information, which is exactly how 404 Media later confirmed the data breach.
Initially, the data breach was discovered by a cybersecurity researcher named Kasra Rahjerdi, who notified Tea immediately.
Tea’s Response
In an official statement from Tea, they confirmed that the breached information included:
“…approximately 13,000 images of selfies or selfies featuring a photo identification submitted during account verification and 59,000 images publicly viewable in the app from posts, comments, and direct messages.”
At first, Tea claimed that the only data leaked was older information from a “legacy data system.” Days later, however, a much more serious data breach was uncovered.
On July 28th, a second data breach was reported by 404 Media, who said that 1.1 million user messages had been leaked. In response, Tea disabled its messaging feature entirely.
Answering 3 Questions About Data Security
-
Absolutely. It’s the industry standard for both large and small companies to use cloud storage to manage their data. When configured correctly and monitored for safety concerns, cloud storage is a powerful tool to keep large amounts of data safe and accessible.
-
Large companies usually have internal IT security divisions that monitor their cloud storage for security risks. Meanwhile, most SMBs (Small and Medium-sized Businesses) rely on managed service providers like us at Omega to provide managed security services.
-
Individuals may be at risk for a data breach if they: frequently use the same password across different accounts, don’t us multi-factor authentication (MFA), or have had personal data exposed in the past and haven’t taken secured their accounts or devices.
Meanwhile, SMBs are at a higher risk for a security breach if they: don’t have dedicated IT (either internal or through a managed service provider), rely on consumer-grade cloud storage such as Dropbox or Google Drive, or aren’t routinely monitoring suspicious activity.
What the Tea Breaches Mean for Cybersecurity in 2025
The Tea breaches remind us of a harsh reality: improperly secured data can be accessed without a company or its consumers even knowing it.
Already, two class-action lawsuits have been filed by Tea users who had their sensitive personal information leaked online. According to privacy technology company Captain Compliance, the California-based users are:
“…leverage the CCPA’s private right of action, which allows statutory damages of $100-$750 per violation for breaches caused by inadequate security, without proving harm. With over 1.7 million users potentially affected, damages could reach hundreds of millions.”
How Companies Can Secure Their Data
If there’s one thing to be learned from Tea, it’s that companies that don’t work with data security professionals shouldn’t assume their data is safe.
Cases like these are exactly why managed service providers like our team at Omega Computer Services exist: to keep your data secure. For more information on our managed security services or to get your data secured by IT professionals, click here to contact us today.